Module 9: Manage Software Deployment Using Group Policy in Windows Server 2016/2019
Examining Software Deployment via Group Policy in Microsoft Windows Server
Software Deployment using Group Policy allows administrators to automatically install, update, or remove software across multiple computers within an Active Directory (AD) environment.
Key Concepts:
Deployment Types:
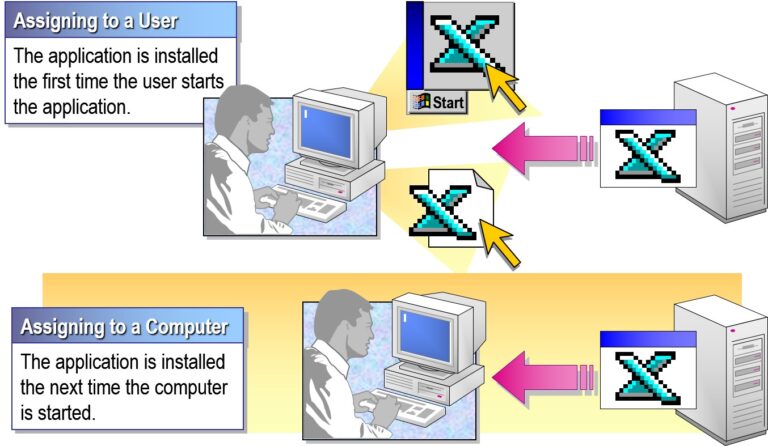
Assigned: Software is installed automatically the next time the computer starts or the user logs in.
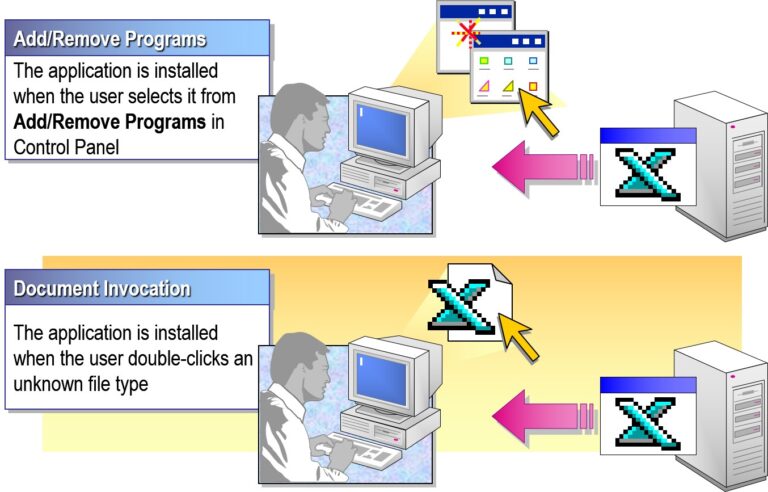
Published: Available in “Add or Remove Programs” for users to install manually (user only, not computer).
Advanced: Offers customization through transforms (.MST files) and settings for deployment behavior.
File Format:
Software must be in MSI (Microsoft Installer) format for direct deployment.Target Scope:
User Configuration: Deploys software based on user login (Published or Assigned).
Computer Configuration: Deploys software to machines (Assigned only).
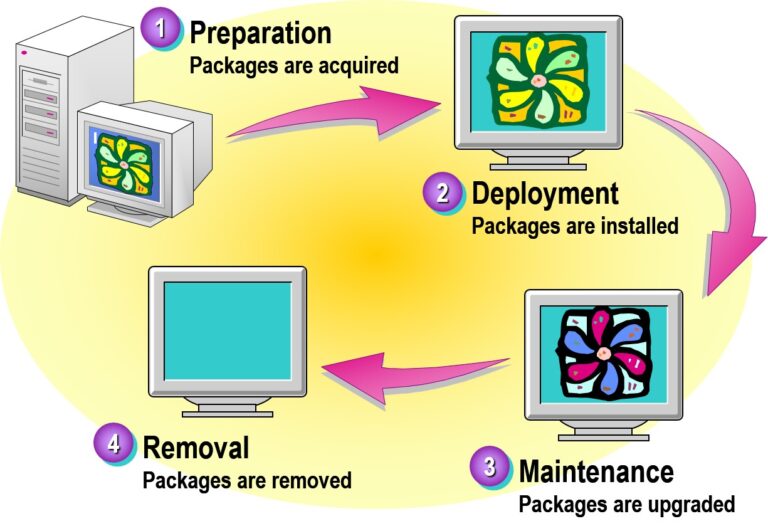
⚙️ Steps for Deploying Software:
Place MSI File on Shared Network Location
(Ensure read permissions for target users/computers)Open Group Policy Management Console (GPMC)
Create or Edit a GPO
Link it to the appropriate AD container (OU, Site, or Domain).Navigate to:
Computer Configuration→Policies→Software Settings→Software Installationor
User Configuration→Policies→Software Settings→Software Installation
Add a New Package
Right-click → New → Package → Browse to the network path → Choose deployment method (Assigned/Published).
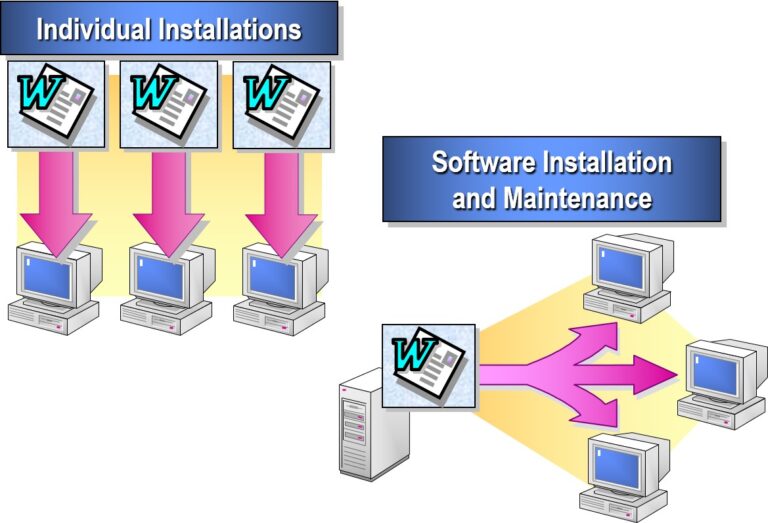
Exploring Software Management Technologies in Microsoft Windows Server
Software Management Technologies are essential tools and services that enable IT administrators to deploy, update, monitor, and maintain software applications across networked environments efficiently.
Key Software Management Technologies:
1. Group Policy Software Installation (GPSI)
Deploys MSI-based applications via Active Directory.
Suitable for small to medium-sized networks.
Supports Assigned and Published deployments.
2. Microsoft Endpoint Configuration Manager (MECM / SCCM)
Enterprise-grade solution for comprehensive software lifecycle management.
Supports deployment of all types of software (EXE, MSI, scripts).
Includes detailed reporting, remote installation, and patch management.
3. Windows Server Update Services (WSUS)
Distributes Microsoft updates (OS, Office, etc.) within a network.
Reduces bandwidth usage by centralizing update downloads.
Provides update approval and scheduling control.
4. Microsoft Intune
Cloud-based software management for modern endpoint environments.
Integrates with Azure Active Directory.
Manages Windows, macOS, iOS, and Android apps from a central console.
5. PowerShell & Scripts
Custom deployment through PowerShell scripts or batch files.
Ideal for custom or advanced installations.
Can be scheduled via Task Scheduler or deployed via GPO or MECM.
6. Windows Package Manager (winget)
CLI-based tool to install, upgrade, configure, and remove software packages.
Ideal for modern automation workflows and DevOps practices.
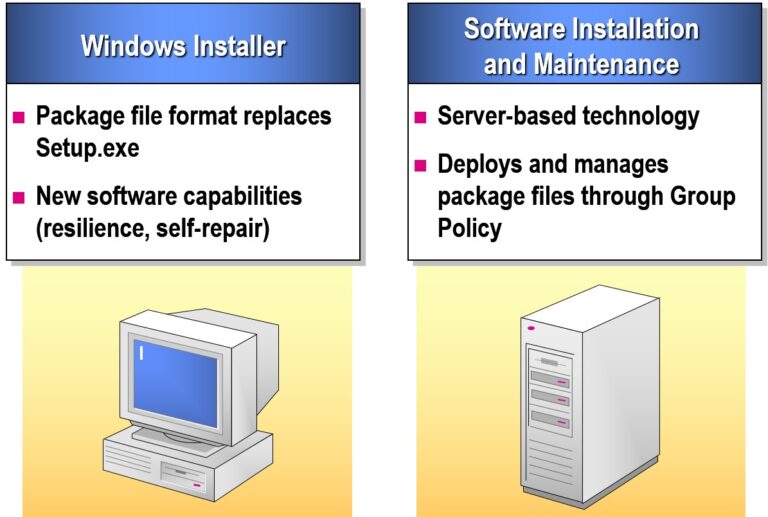
Examining the Software Life Cycle
The Software Life Cycle refers to the structured process of planning, developing, deploying, maintaining, and retiring software applications. In enterprise and server environments like Microsoft Windows Server, managing this life cycle effectively is crucial to ensure security, stability, and performance.
Phases of the Software Life Cycle
1. Planning
Define business needs and software requirements.
Evaluate compatibility with current infrastructure.
Perform cost-benefit analysis and licensing checks.
2. Acquisition or Development
Choose between custom-developed, open-source, or commercial (COTS) software.
Ensure alignment with IT policies (security, scalability, compliance).
3. Testing
Validate functionality in test/staging environments.
Ensure integration with Active Directory, databases, and existing apps.
Perform security testing and performance benchmarking.
4. Deployment
Use tools like Group Policy, SCCM, Intune, or WSUS.
Schedule rollouts to avoid user downtime.
Create rollback plans and system snapshots.
5. Maintenance & Updates
Apply patches, service packs, and hotfixes regularly.
Monitor performance using tools like Event Viewer, Resource Monitor, or third-party APMs.
Manage support contracts and vendor updates.
6. Retirement or Replacement
Phase out outdated or unsupported software.
Migrate user data and configurations.
Ensure secure removal and license termination.
Deploying Software in Windows Server Environments
Software deployment is the process of distributing and installing applications across multiple systems within a network. In enterprise and server environments, this process must be secure, scalable, and automated for efficiency and consistency.
Key Methods of Software Deployment
1. Group Policy Object (GPO)
Tool: Active Directory Group Policy
Package Type:
.msionlyUse Case: Ideal for deploying software across multiple domain-joined machines.
Benefits: Centralized control, no third-party tools needed.
2. System Center Configuration Manager (SCCM) / Microsoft Endpoint Configuration Manager
Supports:
.msi,.exe, scripts, drivers, patchesUse Case: Enterprise-level deployments
Features: Scheduling, reporting, software metering, rollback
3. Windows Deployment Services (WDS)
Primary Use: Deploying OS and pre-installed software images
Supports: PXE boot-based deployment
Benefit: Ideal for new PC rollouts with standardized setups
4. Microsoft Intune (Cloud-Based)
Type: Modern device management for hybrid/cloud environments
Supports: Windows 10/11, mobile devices, MDM policies
Benefit: Ideal for remote teams or BYOD environments
5. PowerShell Scripts
Automate
.msior.exeinstallationsUseful for task automation, error logging, and silent installs
Manual Installation (Small Environments)
Direct installation on each system
Not scalable or recommended for large networks
- Deploying a New Application
- Testing Application Deployment
- Using a Testers Group
- Remove Permissions for Authenticated Users
- Grant Permissions to Testers Group
- Apply Group Policy and Test
- Reinstate Permissions for Authenticated Users
- Using Auto-Install
- Apply Group Policy and Disable Auto-Install
- Test Deployed Software Using Add/Remove Programs
- Enable Auto-Install
- Assigning Software Packages
- Publishing Software Packages
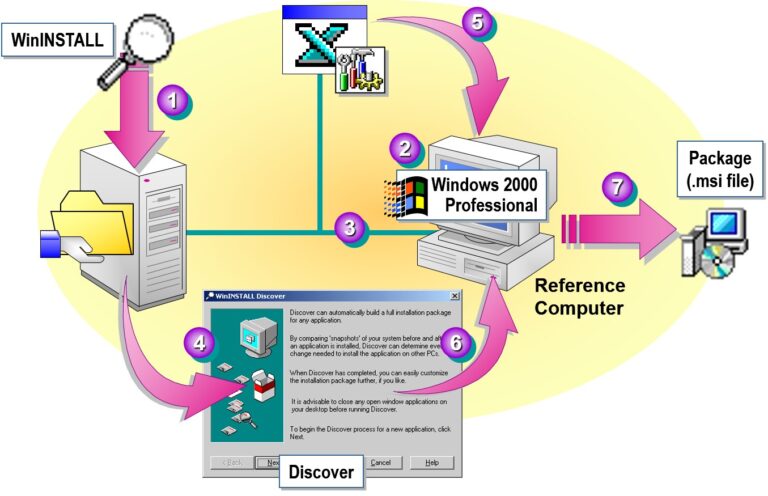
- Repackaging Software Applications
- Publishing Non-Windows Installer Packages
- Limitations of Deploying Non-Windows Installer Packages
- Applications can only be published
- Applications do not automatically repair themselves
- Applications require user intervention to be installed
- Applications cannot be installed with elevated privileges(User must have install rights)
- Using Software Modifications
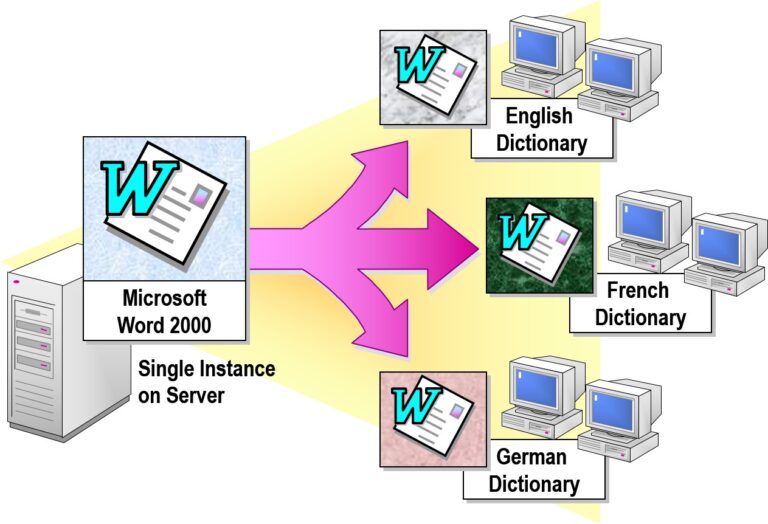
Upgrading Software
- Deploying a Mandatory Upgrade
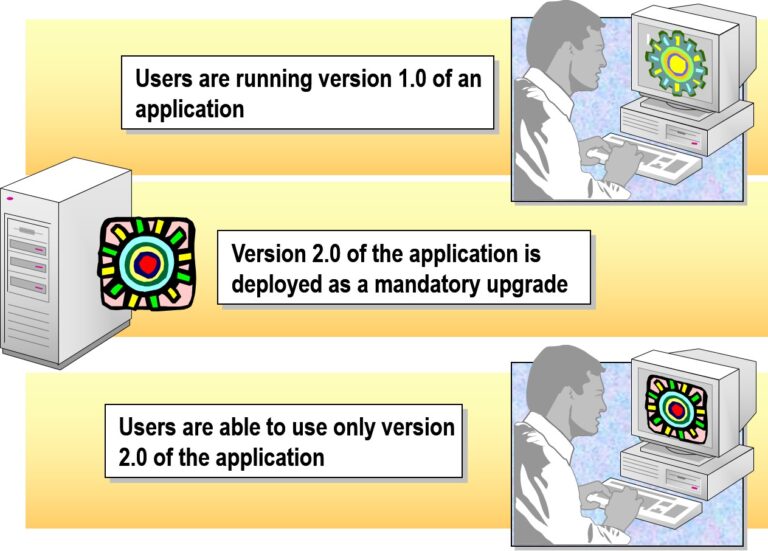
- Deploying an Optional Upgrade
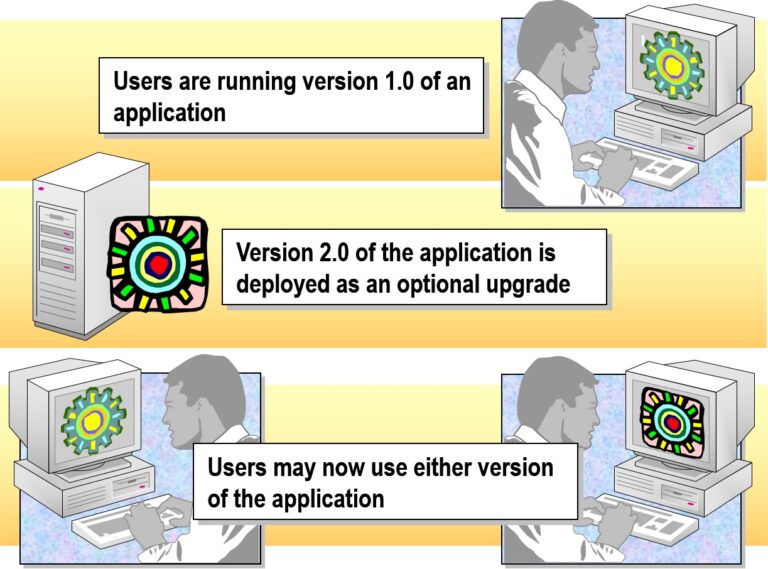
- Redeploying Software
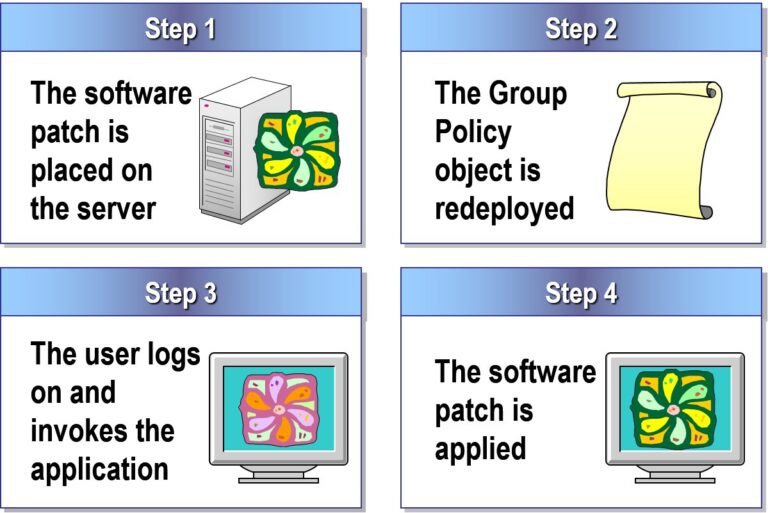
- Software is automatically deleted from a computer, and cannot be reinstalled
- Software is not deleted from a computer, but can no longer be installed
- Only software that was installed from a Windows Installer package file can be removed through Group Policy
- Associating File Extensions
- To prevent users from associating the wrong program with a file type
- Creating Software Categories
- To prevent users from installing too many applications
- Modifying Deployment Options
- To prevent users from installing the wrong application
- Associating File Extensions with Applications
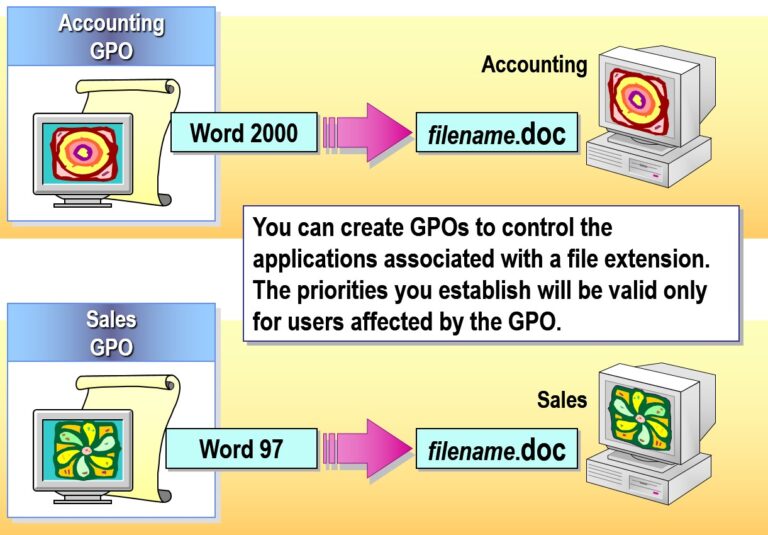
- Modifying Deployment Options
- Change the Deployment Type
- Disable Auto-Install
- Automatically Uninstall Software
- Do Not Display in Add/Remove Programs
- Installation User Interface
- Verify that the application appears in Add/Remove Programs
The error or message “Verify that the application appears in Add/Remove Programs” typically appears when you’re deploying software via Group Policy (GPO) using a .msi file, and the installation is either:
Not executing properly
Not being registered with Windows Installer
Or the
.msilacks required metadata to appear in “Add or Remove Programs” (now called “Apps & Features” in Windows 10/11)
Common Causes & Fixes:
✅ 1. MSI Package Is Invalid or Corrupted
Fix: Test the
.msimanually by double-clicking it on a client machine.
If it installs but does not appear in Add/Remove Programs, it’s missing registry keys like:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall
2. Application Installs but Is Not “Registered”
The MSI might install files but not register itself properly with Windows.
Fix: Repackage or convert the
.exeto a proper.msiusing tools like:Advanced Installer
MSI Wrapper
Inno Setup to MSI converters
✅ 3. Wrong Deployment Method
If you’re deploying an
.exeinstead of.msivia GPO, it won’t be tracked in Add/Remove Programs.Fix: Use a startup script via GPO or deploy via SCCM or Intune if using
.exe.
✅ 4. Install Scope Mismatch
If MSI installs per-user, it won’t appear under Add/Remove Programs for all users.
Fix: Ensure the MSI installs in per-machine mode, using:
msiexec /i yourfile.msi ALLUSERS=1
How to Verify Correct Registration:
Check this registry key on the installed machine:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall\
Or on 64-bit systems:
HKEY_LOCAL_MACHINE\Software\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\
- Verify access to the network distribution point
Common Causes & Fixes:
✅ 1. UNC Path is Incorrect or Inaccessible
GPO deployments require a valid UNC path (e.g.,
\\SERVER\Share\app.msi), not a mapped drive (e.g., Z:).Fix: Make sure the path is:
Correct
Shared with appropriate permissions
Always using UNC format
✅ 2. Share or NTFS Permissions Are Insufficient
The computer or user account must have read access.
Fix: On the shared folder:
Share Permissions: Allow
EveryoneorDomain Computersto have at least ReadNTFS Permissions: Also allow
Readto the same group
✅ 3. Client Cannot Connect to Network During Boot
In WDS or RIS, if the client can’t connect to the network during pre-boot, it can’t load the image or installer.
Fix:
Ensure PXE boot is properly configured
Network drivers are included in boot image
DHCP and TFTP services are running and accessible
✅ 4. Firewall or Antivirus Blocking Access
Security software can block access to SMB shares or port 445.
Fix:
Temporarily disable firewalls or security software
Whitelist the network share
✅ 5. DNS or Network Issues
Client machine may not be able to resolve the hostname of the server.
Fix:
Test
ping SERVERNAMEfrom the clientUse FQDN if needed:
\\server.domain.local\Share
✅ 6. SMB Protocol Disabled
Windows 10/11 might have SMBv1 disabled by default.
Fix:
Ensure the server supports SMBv2 or SMBv3
Avoid using legacy SMBv1 shares
- Look for Group Policy conflicts when deployment problems arise
Common Group Policy Conflicts to Look For:
✅ 1. Multiple GPOs Configuring the Same Setting
If multiple GPOs are applied to a user/computer and they configure the same setting (e.g., software deployment, folder redirection), the last applied GPO wins based on the processing order (LSDOU: Local, Site, Domain, OU).
Fix:
Use Group Policy Modeling (Resultant Set of Policy – RSoP) to trace which GPO is actually taking effect.
Consolidate conflicting GPOs or use WMI filtering or security filtering to scope them properly.
✅ 2. GPO Not Linked to the Right OU
The policy might exist but isn’t linked to the OU containing the target computers or users.
Fix:
In Group Policy Management, make sure the GPO is linked to the correct Organizational Unit (OU).
The target machine or user must reside in that OU.
✅ 3. Security Filtering or WMI Filtering Preventing Application
GPOs can be scoped to specific users/groups or filtered by WMI queries.
If the computer/user doesn’t match the filter, the policy will not apply.
Fix:
Check the Security Filtering tab in GPMC.
Use
gpresult /rorrsop.mscon the client to verify whether the GPO is being applied.Check WMI filter logic — make sure it’s accurate for OS version, hardware, etc.
✅ 4. Slow Link Detection or Offline Mode
Group Policy has a feature to skip software installations over slow links.
Fix:
In GPMC:
Computer Configuration > Policies > Administrative Templates > System > Group Policy > Group Policy slow link detectionSet to
0(disable slow link detection) to avoid skipping GPOs.
✅ 5. Loopback Processing Conflicts
If loopback processing is enabled (
MergeorReplace), user policies might be overridden based on the computer they log into.This is common in terminal servers, kiosks, or labs.
Fix:
Check
Computer Configuration > Administrative Templates > System > Group Policy > User Group Policy loopback processing modeEnsure it’s intentional and not conflicting with other user GPOs.
✅ 6. Timing Conflicts
If the GPO deploys software at startup, but the network isn’t ready yet, the installation might fail.
Fix:
Enable “Always wait for the network at computer startup and logon”:
Computer Configuration > Policies > Administrative Templates > System > LogonSet to
Enabled
✅ 7. Software Already Installed Manually or Conflicts with Other GPO Installs
Manual installations or another GPO installing a different version can block the GPO’s
.msifrom applying.Fix:
Check installed applications on client.
Avoid deploying conflicting or multiple versions of the same software.


Add comment