Introduction to Active Directory
Active Directory (AD) is a directory service by Microsoft that helps manage users, computers, and resources in a Windows network by organizing them into a secure, hierarchical structure.
What Is Active Directory?
Active Directory (AD) serves as the cornerstone of modern IT infrastructure, providing a centralized platform for managing users, devices, and resources across an organization. Its hierarchical structure and integration capabilities simplify administrative tasks, enhance security, and enable seamless scalability for businesses of all sizes.
Active Directory Supported Technologies
Active Directory (AD) supports a wide range of technologies to provide centralized identity and access management across networks. Key supported technologies include:
DNS (Domain Name System) – Critical for locating domain controllers and services in an AD environment.
LDAP (Lightweight Directory Access Protocol) – Used for querying and modifying items in AD.
Kerberos Authentication – Default secure authentication protocol in AD environments.
Group Policy – Enables centralized management and configuration of operating systems, applications, and users.
NTLM (NT LAN Manager) – Legacy authentication protocol, supported for backward compatibility.
Certificate Services – For managing digital certificates and public key infrastructure (PKI).
PowerShell – Extensively used for automating AD administrative tasks.
DFS (Distributed File System) – Enables shared file access across multiple servers with consistency.
Active Directory Federation Services (AD FS) – Provides single sign-on (SSO) across different networks.
Active Directory Certificate Services (AD CS) – Issues and manages security certificates.
Active Directory Rights Management Services (AD RMS) – Protects digital information from unauthorized use.
Replication Services – Ensures consistency of directory data across domain controllers.
Active Directory Naming Conventions
Active Directory (AD) naming conventions are structured rules and best practices used to name objects such as domains, users, computers, organizational units, and more. These conventions help maintain clarity, consistency, and scalability in enterprise environments.
1. Domain Naming Conventions
Should resemble DNS naming (e.g.,
corp.example.com)Use lowercase letters for consistency
Avoid special characters and underscores
Recommended to use publicly registered domain names
📌 Example: ad.skillpointit.com
✅ 2. Organizational Unit (OU) Naming
Reflect the function or department (e.g., HR, IT, Finance)
Use PascalCase or kebab-case
Avoid spaces and special characters
📌 Example: HR_Department, IT-Support
✅ 3. User Account Naming
Use consistent format:
firstname.lastname,firstinitiallastname, oremployeeIDAvoid special characters and spaces
Use lowercase for email compatibility
📌 Examples:
john.smithjsmithE123456
✅ 4. Computer Naming
Should indicate location, department, and unique ID
Use uppercase for visibility in legacy systems
Avoid spaces and keep names under 15 characters
📌 Example: LHR-IT-WS001
(Location-Dept-Device#)
✅ 5. Group Naming
Prefix based on group type:
GRP_,DL_,SEC_Include role or purpose in the name
📌 Examples:
DL_HR_Managers(Distribution List)SEC_IT_Admins(Security Group)
✅ 6. Service Account Naming
Prefix with
svc_orsa_Include application name and environment
📌 Example: svc_SQLBackup_Prod
- Active Directory and DNS – Relationship Explained
Active Directory (AD) and Domain Name System (DNS) are tightly integrated and work together to ensure the smooth functioning of a Windows Server domain environment.
- What is DNS?
DNS (Domain Name System) is a service that translates human-readable domain names (like example.com) into IP addresses (like 192.168.1.1).
- Why DNS is Crucial for Active Directory
Active Directory relies on DNS for:
Domain controller discovery
Service location (SRV records)
Authentication and logon processes
Without DNS, Active Directory cannot function properly.
Logical Structure of Active Directory
The logical structure of Active Directory (AD) defines how resources are organized, grouped, and managed within a Windows domain environment—independent of the physical network layout.
- Domains
- Security Boundary
A security boundary is a limit within a network or system that defines and enforces security policies, such as authentication, authorization, and access control. In Active Directory, a domain acts as a primary security boundary, meaning users and resources within that domain are governed by a common set of security rules and trust relationships.
- Unit of Replication
A Unit of Replication in Active Directory refers to the smallest portion of directory data that can be replicated between domain controllers. Typically, this unit is the naming context or directory partition, such as:
Domain partition (contains user, group, and computer objects)
Configuration partition
Schema partition
Application partition (optional)
- Domain Modes
Domain Modes in Active Directory determine the available features and compatibility level of a domain based on the versions of Windows Server running on the domain controllers.
Windows 2000 Mixed Mode
Supports Windows NT 4.0 BDCs (Backup Domain Controllers).
Limited AD features.
Windows 2000 Native Mode
All domain controllers must be at least Windows 2000.
Enables full AD features like group nesting and universal groups.
Windows Server 2003 / 2008 / 2012 / 2016 / 2019 / 2022 Domain Functional Levels
Each higher level unlocks advanced features like:
DFS improvements
Fine-grained password policies
Authentication enhancements
Recycle Bin (from 2008 R2 and above)
- Organizational Units
- OU Hierarchy
Organizational Unit (OU) Hierarchy in Active Directory is a logical structure used to organize and manage users, groups, computers, and other resources within a domain.
- Administrative Control of Organizational Units (OUs)
Administrative Control of OUs in Active Directory refers to the ability to delegate specific administrative tasks over certain parts of the directory structure without giving full control of the domain.
- Organizational Units (OUs) and the Single Domain Model
In a Single Domain Model, Organizational Units (OUs) are used to logically organize and manage resources within one domain of an Active Directory environment.
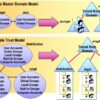
- Trees and Forests in Active Directory
Trees and Forests are the topmost logical structures in Active Directory (AD) used to organize and manage multiple domains in a secure, hierarchical, and scalable environment.
- Tree (Domain Tree):
A Tree is a group of one or more domains that share:
A contiguous namespace (e.g.,
corp.com,hr.corp.com)A transitive trust relationship between them
- Forest:
A Forest is the highest level of the AD structure that can contain:
One or more trees
A global catalog for searching across domains
Universal trust relationships between trees
- Schema in Active Directory
The Active Directory Schema is the blueprint or structure of the entire directory. It defines:
Physical Structure
- Sites
- Domain Controllers
Specific Domain Controller Roles
- Global Catalog Server
- Single Master Operations (FSMO Roles) – Explained
In Active Directory (AD), Single Master Operations are specialized tasks handled only by specific Domain Controllers (DCs) to avoid data conflicts. These tasks are called FSMO Roles (Flexible Single Master Operations).
- Schema Master
- Domain Naming Master
- RID Master
- PDC Emulator
- Infrastructure Master
Installing Active Directory
- Preparing to Install Active Directory
- Active Directory Installation Requirements
- Active Directory Implementation Plan
- Installation Options
- Establishing the Root Domain in Active Directory
The Root Domain is the first domain created in a new Active Directory (AD) forest. It acts as the foundation for the entire AD hierarchy and is the topmost parent of all domains in the forest.
- Start Installation Wizard
- Select Domain Controller and Domain Type
- Specify Required Information
- Domain, DNS, and NetBIOS names
- Database, log, and shared system volume locations
- Select to weaken permissions
- Active Directory Is Installed
- Computer Is Domain Controller
- Active Directory Tools Added
- Adding a Domain Controller to an Existing Domain in Active Directory
Adding a domain controller (DC) to an existing domain enhances availability, fault tolerance, and load balancing within an Active Directory environment. The new DC will replicate directory data from existing controllers and share domain services.
Steps to Add a Domain Controller:
Install AD DS Role:
Go to Server Manager → Add Roles and Features
Select Active Directory Domain Services → Complete wizard
Promote Server to a Domain Controller:
After installation, click Promote this server to a domain controller
Choose:
Add a domain controller to an existing domain
Enter Domain Information:
Provide domain name (e.g.,
skillpointit.local)Provide Domain Admin credentials
Select Domain Controller Capabilities:
✔️ Domain Name System (DNS)
✔️ Global Catalog (GC)
❌ (Optional) Read-only Domain Controller (RODC)
Configure Paths:
Default paths for NTDS, SYSVOL, and logs
Customize if needed
Review and Install:
Validate all settings
Begin installation
Server will reboot automatically
- Start Installation Wizard
- Select Domain Controller and Domain Type
- Specify Required Information
- Network credentials
- DNS name of domain to join
- Database, log, and shared system volume locations
- Active Directory Is Installed
- Creating a Child Domain in Active Directory
A child domain is a subdomain within an existing Active Directory domain hierarchy. It extends the namespace of a parent domain and is used to provide delegated administration, organizational separation, and geographical structure in enterprise environments.
- If your parent domain is:
- skillpointit.com
- Then a child domain would be:
- training.skillpointit.com
Steps to Create a Child Domain:
1. Install AD DS Role (if not already installed):
Open Server Manager
Choose Add Roles and Features
Select Active Directory Domain Services
2. Promote the Server:
After role installation, click Promote this server to a domain controller
3. Select Deployment Type:
Choose:
Add a new domain to an existing forest
→ Then select:Child Domain
4. Enter Child Domain Info:
Parent Domain:
skillpointit.comNew Child Domain Name:
trainingResulting FQDN:
training.skillpointit.com
5. Provide Credentials:
Use Enterprise Admin credentials from the parent domain
6. Configure Domain Controller Options:
Choose options like:
DNS Server
Global Catalog
RODC (if applicable)
7. Set Directory Paths & Confirm:
Confirm the NTDS, SYSVOL, and log folder locations
Review the summary
Install and reboot
- Creating a Tree in an Existing Active Directory Forest
A Tree in Active Directory is a new domain that has a distinct DNS namespace from the existing domains in the forest, but still shares a common schema, global catalog, and configuration. Trees are used when you need separate DNS namespaces while maintaining trust relationships and unified directory services within a single forest.
- You already have a root domain:
- skillpointit.com
- Now, you want to create a new tree:
learntech.org“ ← Different namespace
This becomes part of the **same forest**, but a **separate tree**.
—
### 🧱 Prerequisites:
– Enterprise Admin privileges
– DNS properly configured
– Server OS: Windows Server 2016/2019/2022
– AD DS role installed
– Static IP address
—
### 🔧 Steps to Create a New Tree in an Existing Forest:
#### **1. Install AD DS Role (if not done already):**
“`bash
Server Manager → Add Roles and Features → Active Directory Domain Services
Promote the Server to Domain Controller:
Open Server Manager
Click “Promote this server to a domain controller”
3. Select Deployment Type:
Choose:
✅Add a new domain to an existing forest
→ Then:
✅Add a new domain tree
4. Enter New Domain Information:
Parent forest:
skillpointit.comNew Tree Name:
learntech.org
5. Provide Enterprise Admin Credentials:
Use credentials from the root domain to authorize the change
6. Configure DC Options:
Select:
DNS Server
Global Catalog
Do not select RODC (unless needed)
7. Complete Installation:
Set folder paths (NTDS, SYSVOL)
Review and confirm
Install → Server will reboot
Verifying Active Directory Installation in Windows Server 2016/2019/2022
Once you’ve installed Active Directory Domain Services (AD DS) and promoted your server to a domain controller, verification is critical to ensure the installation was successful and fully functional.
- Verifying SRV Resource Records
- With DNS in MMC
- Find Netlogon.dns in systemroot/System32/Config
- Verifying Server Promotion
- Database
- Shared System Volume
- Default First Site Name
- Global Catalog Server
- Root Domain
- Default Containers
- Default Domain Controllers OU
- Verify SRV Resource Record Registration
Flexible Single Master Operations (FSMO) roles are special responsibilities assigned to one or more Domain Controllers (DCs) in an Active Directory (AD) environment. Proper management ensures domain consistency, prevents conflicts, and keeps AD functioning correctly.
What Are FSMO Roles?
FSMO roles are 5 critical roles in Active Directory divided into two categories:
🔹 Forest-Wide Roles (Only 1 per forest):
Schema Master – Controls all updates and modifications to the AD schema.
Domain Naming Master – Manages additions/removals of domains in the forest.
🔹 Domain-Wide Roles (1 per domain):
RID Master – Allocates pools of unique IDs to DCs for creating security objects.
PDC Emulator – Acts as a time source, password update authority, and backward compatibility with older systems.
Infrastructure Master – Updates group membership references across domains.
The Domain Administrator account is a built-in, highly privileged user account that has full access to manage all components of an Active Directory domain.
Common Tasks Performed Using the Domain Admin Account:
Create/Manage User Accounts
Configure Group Policies (GPOs)
Add/Remove Domain Controllers
Install Active Directory Roles and Features
Manage DNS, DHCP, and other core services
Access and manage file shares and permissions
Audit logs and event viewer for security tracking
Perform backups and system restores
Delegate permissions and OU administration

Add comment